What Is DKIM? DomainKeys Identified Mail & DKIM Records
Email-based attacks and malicious emails are a serious threat to all who communicate online. Many of these attacks, like spam and phishing messages, come from spammers attempting to impersonate you or your brand.
Therefore, ensuring the authenticity of email messages is crucial. One of the most common ways of doing this is through DomainKeys Identified Mail. In this article, learn what DKIM is, how it works, and how to set it up.
What is DKIM?
DomainKeys Identified Mail (DKIM) is a protocol for verifying the authenticity of email messages. This technique helps detect whether someone altered the messages in transit between the sending and receiving mail servers.
Malicious actors may try to intercept sent emails to carry out phishing attacks; therefore, the DKIM will use unique private-public key cryptography to verify the email content and protect against forged emails.
The DKIM protocol is formally defined in Internet Engineering Task Force RFC 6376, DomainKeys Identified Mail Signatures. DomainKeys Identified Mail permits organizations that own the signing domain to claim responsibility for sent emails by associating them with that domain.
Organizations add a DKIM signature to each email message they send. The recipients that receive these emails authenticate them. A private key only known to the sender's email servers typically creates the signature.
The protocol works closely with the Sender Policy Framework (SPF) and Domain-based Message Authentication Reporting and Conformance (DMARC) protocols to create a comprehensive email security ecosystem. Otherwise, if spammers manage to impersonate an email domain or domain owner, they would use it for direct domain spoofing attacks.
These three protocols publish all the information used for email authentication in the form of DNS TXT records. Any email that doesn't pass DomainKeys Identified Mail and Sender Policy Framework receives a spam marking and fails to pass through the email server. The protocol is essentially an added layer of authentication for email. Most email services, like Gmail, Yahoo, and Outlook support DKIM to authenticate outgoing emails and check signatures on incoming emails.
Key components of DKIM
DomainKeys Identified Mail consists of key components that work together to ensure email authenticity. The main components of DKIM include the public key, the private key, the signature, the record, and the header.
Public key
The public DKIM key is published to your domain's domain name system (DNS) records. It allows email receivers to verify a digital signature. Anyone can access it, but recipients use the key to authenticate that email claiming to come from your domain did receive a signature from your private key.
Private key
The sender uses the private key to generate the digital signature from the signing domain. The signature is included with the email in the header.
DomainKeys Identified Mail signature
The DKIM signature is a digital signature that gets added to each sent email message. The signing domain's private key creates this digital signature. It's simply the encrypted hash of the email header and body.
DomainKeys Identified Mail header
The DKIM header goes on each email message that leaves the server. The header contains information about the signature, like the signing domain and DKIM selector.
In addition to these main components, DKIM also includes components such as:
- DKIM selector. This is a unique identifier that identifies the DKIM signature. Companies use DKIM keys or selectors for marketing emails.
- Signature verification. This is the process of verifying the digital signature using the public key.
- Body hash. This is the hash of the email body. It verifies that the email message remained the same along its path.
- Cryptographic algorithm. These establish the set of rules followed or used to create the DomainKeys Identified Mail signature.
- Timestamp. The timestamp refers to the creation time of the DomainKeys Identified Mail signature. This timestamp helps to prevent replay attacks.
How does DKIM work?
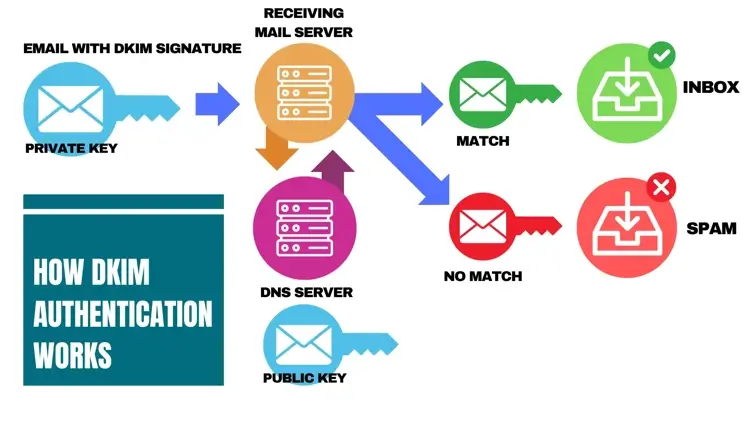
DKIM emerged out of the need to increase security in online communications. As such, it uses asymmetric cryptography to sign emails. The process works using a key pair made up of a private key and a public key. The sender uses a private key to sign the email, and the recipient uses the corresponding public key to verify the signature.
When you send an email, the sending server creates a DKIM signature. The system then calculates the hash of the message, including the body and headers of your message, using a private key. Within a short time, the message arrives at the receiving server,.
Once the email arrives, the recipient's server calculates the hash again and decrypts the signature using the public key. If the hashes match, the signature is valid. It means that nobody tampered with the email during the transfer and the original message comes from the claimed sender.
If the signatures don't match, authentication fails, because someone likely changed the message body in some way. Your email will likely go to the spam folder.
Note that your listed domain or your SMTP server stores your private key. The domain name system publishes the public key.
Example of a DKIM signature
DKIM signatures begin with the string DKIM-Signature followed by tag values and separated by semicolons. Consider the following example and its breakdown:
DKIM-Signature:v=1;a=rsa-sga256;d=example.com;s=selector1-example-com;t+1666050599;h=From:To:Message-ID:Subject:MIME-Version:Content-Type;bh=dGjLiHNha2UgYmVIIGZpbmVk;b+aHR0cDovL3d3dy5leGFtcGxILmNvbS9zdWJzY3JpYmVyL2RpZ2lzdC9zdWJzy3JpYmVyL2ZpbmRiZC5wZW
| Tag Value | Explanation |
| v=1 | The version of the DKIM protocol in use; in this case, Version 1 is in use. |
| a=rsa-sha256 | The cryptographic algorithm SHA-256 secure hash is used to create the digital signature. |
| d=example.com | Specifies the domain associated with the key. The owner of the signing domain example.com claims responsibility for the email messages. |
| s=selector1-example-com | Refers to the DKIM selector, which identifies a specific DKIM public key used to sign emails. |
| t=1666050599 | t refers to the timestamp, which is the number of seconds elapsed and the time at which the signature was created. |
| h=From:To:Message-ID:Subject:MIME-Version:Content-Type | This indicates the list of header fields that were signed. |
| bh=dGh|IHNha2UgYmV|IGZpbmVk | This is the hash of the email body content. |
| b=aHR0cDovL3d3dy5leGFtcGx|LmNvbS9zd WJzY3JpYmVyL2RpZ2|zdC9zdWJzY3JpYmVyL2ZpbmRIZC5wZW | This is the actual signature generated using the private key associated with the sending domain. |
Why use DKIM?
DomainKeys Identified Mail provides several benefits for emails. It:
- Improves email deliverability. By proving the legitimacy of email with DKIM verification, it increases the chances of the email reaching the recipient's inbox rather than receiving a spam mark.
- Minimizes domain spoofing. Implementing DomainKeys Identified Mail can improve the reputation of the sender's domain, which then leads to increased trust from recipients. An email an attacker sends through your domain fails to authenticate because it lacks your private signature.
- Prevents email alterations. It helps verify the authenticity of the sender, ensuring the security of the email. The digital signature serves as a failsafe that no one can decrypt even if someone intercepted the mail.
- Protects against phishing attacks. DomainKeys Identified Mail helps protect against phishing attacks by verifying the sender's identity, which then prevents attackers from impersonating a legitimate domain.
- Supports email authentication. DomainKeys Identified Mail works alongside other email authentication protocols, such as SPF and DMARC, to provide an additional layer of security. This prevents unauthorized use of a domain.
How to set up DKIM
Setting up DomainKeys Identified Mail involves three steps to enable email authentication of outgoing emails.
Step one: Generate DKIM keys
We've seen that keys are generated using a cryptographic algorithm. You can use tools such as OpenDKIM or DKIM-Gen. These tools generate a pair of keys: a private one and a public one. The private key must be securely stored, while the public key is added to the DNS TXT record of the domain.
Remember to regularly rotate DKIM keys to maintain security and prevent unauthorized access to your emails.
Step two: Add DKIM records to DNS
To add DKIM records to your DNS, you need to generate a key pair using a tool or service. Then, create a TXT record in your DNS zone with the generated public key. Next, publish the DKIM selector in the TXT record. Once the DKIM records are added to your DNS, they will be used by email servers to authenticate the origin of your emails.
Step three: Test DKIM configuration
To ensure that you correctly set up your DKIM configuration, perform the following tests:
- Email sending test. Send an email from your domain and check if the signature is present in the email header.
- Email receiving test. Send an email to a test mailbox and then check if the DKIM signature is verified by the receiving server.
- DKIM record check. Use a DKIM checker tool to verify DKIM records received the correct setup in your DNS.
That way, you'll know whether or not your configuration is working as intended.
Limitations of DKIM
DKIM is essential for email authentication. However, just like with everything else, it has limitations. Because of these limitations, scammers could execute potential email attacks from anywhere. You might see a mismatched signature, for example; DomainKeys Identified Mail offers a level of email sender authenticity through domain validation, but it doesn't provide personal identity verification.
Additionally, if someone compromises the private key used for DomainKeys Identified Mail, attackers can send fraudulent emails that appear authentic. Also, the protocol doesn't stop phishing attempts. It makes it difficult for bots to attack because they need private keys, but it isn't impenetrable. Therefore, it must work with DMARC and SPF to deliver the right results.
Comparing DKIM vs DMARC
DMARC protocol, which stands for Domain-based Message Authentication, Reporting, and Conformance, operates on top of DomainKeys Identified Mail and SPF to further protect your email infrastructure. The main purpose of DMARC is to unify DomainKeys Identified Mail and SPF authentication methods into a common mechanism.
It describes the next step to take with an email that fails SPF and DomainKeys Identified Mail. DMARC policies tell the recipient what step to take next. These steps, or policies, may include:
- Nothing. The policy tells the receiving email server to take no action if an email fails DMARC authentication. This means the email will go to the recipient's inbox even if it's likely spam.
- Quarantine. It instructs the email server to put unauthenticated messages in the recipient's spam folder rather than deliver them outright.
- Reject. This option tells email servers to discard the email, meaning the email does not go to the recipient at all.
These policies are stored as DNS TXT records, much like DKIM records. Together, DMARC, DKIM, and SPF provide the best results for email security.
Frequently asked questions
Do I need a certificate to run DKIM?
No, you don't need a certificate to run DKIM validation; however, it gives users an efficient way to authenticate outgoing messages.
Does DKIM ensure emails have end-to-end encryption?
No. It focuses on email encryption, but it doesn't provide encryption for the actual email content.
What is a DKIM lookup tool used for?
A lookup tool performs a DKIM check to inspect if your record is valid and the signature is legitimate.